A recent investigative report has uncovered a connection between the Belsen Group and ZeroSeven Group, with both having connections to Yemen. The Belsen Group was spotlighted for leaking Fortinet data and selling network access.
Belsen Group
- The Belsen Group first appeared on cybercrime forums in early January 2025 under the alias Belsen_Group.
- Their Initial activity was dumping 1.6 GB of sensitive data from over 15,000 vulnerable Fortinet FortiGate devices.
- The data dumped were IP addresses, configurations, and VPN credentials, which were first shared on BreachForums and later posted on their dedicated TOR-based blog.
- To get attraction they released it for free.
- Following the data dump, the group began selling network access to victims in Africa, the USA, and Asia.
Note: Belsen Group is believed to have exploited CVE-2022-406841, a critical authentication bypass vulnerability in FortiGate firewalls, suggesting they may have had access to this data for more than two years before the leak.
ZeroSevenGroup
- ZeroSeven group initially appeared in July 2024 on NulledTo before expanding to BreachForums, CrackedTo, and Leakbase.
- This group’s main focus is on leaking and selling stolen data and network access, targeting companies in Poland, Israel, the USA, UAE, Russia, and Brazil.
- The group initially offered free leaks but later began selling databases(hosted on Mega or Terabox).
- In August 2024, they claimed responsibility for breaching Toyota’s US branch, leaking 240GB of sensitive data.
- There is a rumour that, ZeroSevenGroup scammed Medusa Ransomware group by selling outdated and fake network access.
- Since January 2025, they have been active on the Exploit Forum, offering C2 and VPN access to an Italian government entity and companies in the US and Japan.
- ZeroSeven group can also traced back to RaidForums, where they operated as “ZeroXGroup” under the username zerox296.
Overlap Between ZeroSevenGroup and Belsen Group
Based on the report, the password shared by ZeroSevenGroup to unlock the early databases led to an email address from a leaked database and a machine infected with info stealer malware using the same password. These were all connected to the Belsen Group. Both the email address and the infected machine were traced to Yemen, with social media links suggesting they were associated with each other.
The evidence that connects both groups are,
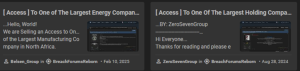
Shared Title Format: Both groups were the only users to use the same title format—“[Access]”—including square brackets and spaces, in their titles and multiple posts.
Similar Phrasing and Style: Their posts often displayed nearly identical phrasing and stylistic patterns, suggesting the use of a same template.
Similar Writing Style: Both groups exhibit a similar writing style with recurring templates.
Are Belsen Group and ZeroSeven Group the Same?
The attribution is the most challenging process, and it often takes years to draw a definitive conclusion. Is there enough evidence to say both groups are the same? While they share similar intentions and focus, it’s also possible that this could be a false flag operation meant to mislead analysts. Although both groups emerged within a short time frame, there could be a connection, but further analysis is needed to confirm this.
Follow us on X and Linkedin for the latest cybersecurity news
Source:hxxps[://]www[.]kelacyber[.]com/blog/could-the-belsen-group-be-associated-with-zerosevengroup