For the last few months, there has been a surge in the distribution of a backdoor known as “DCRat” in the gaming community. This backdoor is available to cybercriminals through a Malware-as-a-Service (MaaS) model. The threat actors also assist cybercriminals in setting up the infrastructure for hosting the C2 servers.
Background
This backdoor is from the remote access trojan (RAT) family called Dark Crystal RAT(RCRat), which has been known since 2018. This trojan can load additional modules to improve its functionality. Over the course, there have been more than 34 distinct plugins surfaced, with the most malicious features including keystroke logging, webcam access, file stealing, and password exfiltration.
Distribution Method
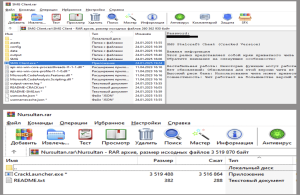
DCRat is distributed via YouTube, where cyber criminals create fake accounts or use compromised ones to upload videos on cheats, cracks, and gaming bots, primarily targeting users of pirated software. The video includes a download link, which leads to a legitimate file-sharing service hosting a password-protected archive. The password for the archive is provided in the video description.
This zip file is loaded with DCRAT trojan and other irrelevant files to distract the downloader.
This backdoor is heavily downloaded in Russia, China, Belarus, and Kazakhstan.
MaaS
We’ve previously explained that this backdoor operates as a Malware-as-a-Service (MaaS). The threat actors provide infrastructure to the cybercriminals allowing them to create third-level domains for hosting C2 servers, primarily in the Russian (RU) zone.
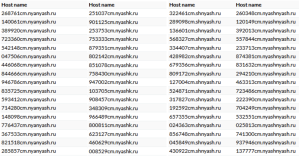
This group has registered more than 50 new second-level domains since the beginning of the fear, with five of them currently hosting more than 40 third-level domains.
A unique feature of this is the frequent use of specific words in the second-level domains of the malicious infrastructure, such as “nyashka,” “nyashkoon,” “nyashtyan,” and others. These terms are very common in Japanese pop culture, particularly among anime and manga fans.
The Bottom Line
Using pirated software goes against copyright laws and can lead to significant issues, as it typically requires activators or cracks that disable antivirus and security features. Cybercriminals often exploit this situation to drop malicious payloads, such as trojans, Ransomware, keyloggers, etc.
Stay Safe !!
Related Reading:
Russian Threat actors Target Ukrainian Defense with DCRAT Malware
Phishing Attack Using OpenAI’s Operator
Follow us on X and Linkedin for the latest cybersecurity news
Source:hxxps[://]securelist[.]com/new-wave-of-attacks-with-dcrat-backdoor-distributed-by-maas/115850/