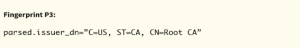After infamous NSO group’s fiasco, another Israeli spyware provider has come under public scrutiny for supplying spyware to major Western governments. Researchers have now mapped out the global infrastructure of this new spyware in a report published on Wednesday.
Background
Founded in Israel in 2019 by former Prime Minister Ehud Barak and ex-Unit 8200 commander Ehud Schneorson
Markets a product called “Graphite” that reportedly focuses on accessing messaging apps rather than taking complete control of devices
Claims to only sell to governments that “abide by international norms and respect fundamental rights”
Recently expanded to the U.S. with a company staffed by former intelligence officials and military personnel
Accquired for $500 million in December 2024 by U.S. private equity firm AE Industrial Partners, with $400 million in additional performance-based payments
Surveillance Reach
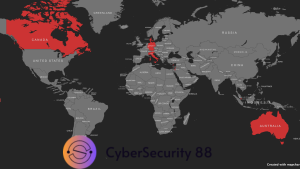
Paragon’s spyware, Graphite, has been deployed in a variety of countries, with evidence surfacing in Australia, Canada, Cyprus, Denmark, Israel, and Singapore. In 2024, investigative researchers mapped out the infrastructure supporting Graphite, which included cloud-based servers and on-premise deployments.
- Tier 1: Victim-facing servers, often associated with command-and-control operations.
- Tier 2: Command infrastructure likely operated by Paragon and its government customers.
Tier 1: Victim-Facing Servers
In 2024, researchers identified a set of infrastructure associated with Paragon’s spyware, specifically its Graphite tool, referred to as Tier 1 servers. The servers were found to be using distinctive self-signed TLS certificates, which helped in identifying them.
Using these fingerprints, researchers traced more than 150 certificates across multiple IP addresses, primarily from cloud-based server rental companies. This Tier 1 infrastructure is crucial because it provides the foundation for the spyware’s command-and-control mechanism, facilitating data exchange with victim devices under specific conditions, allowing spyware operators to monitor and control infected targets.
Tier 2: Paragon and Customer Endpoint
Tier 2 Server is directly linked to Paragon’s customer deployments and these servers are found in Israel, Australia, Canada, and Singapore. Unlike Tier 1 servers hosted on cloud services, Tier 2 infrastructure was often hosted by local telecom operators, raising the likelihood that these servers were operated by Paragon or its government customers directly.
This setup allows for more localized control on Graphite and likely contains customer-specific customization. The presence of unique codenames related to countries where these deployments occurred also indicates the potential involvement of governmental or law enforcement.
Certificates matching Fingerprint P3 were found on static IPs in Israel, further reinforcing the link to Paragon. The presence of Fingerprint P4—a certificate with the name “installerserver” and an organization labeled “Graphite”—was also identified within this infrastructure, suggesting that the servers in this tier are involved in deploying and maintaining Paragon’s spyware on targeted devices.
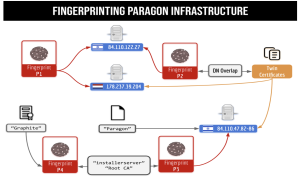
Mapping Paragon’s global infrastructure
Researchers developed four distinct cryptographic fingerprints to identify Paragon’s infrastructure:
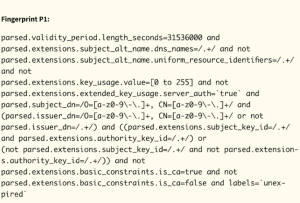
Fingerprint P1: Identified victim-facing TLS certificates with distinctive properties:
- 1-year validity period (31536000 seconds)
- DNS names in subject alternative name
- Missing key usage extensions
- Missing serverAuth in extended key usage
- Distinctive subject and issuer distinguished name format
- 150 matching certificates discovered
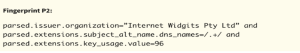
Fingerprint P2: Identified a second tier of infrastructure based on certificates with:
- “Internet Widgits Pty Ltd” in issuer organization
- DNS names in subject alternative name
- Key usage value of 96
- 47 certificates matched this fingerprint
Fingerprint P3: Located Paragon’s operational dashboard interfaces with certificates having:
- Issuer DN with “C=US, ST=CA, CN=Root CA”
- 8 certificates identified with this fingerprint
Fingerprint P4: Found “installerserver” certificates with:
- Subject common name “installerserver”
- Issuer common name “Root CA”
- One certificate discovered with organization name “Graphite”
The technical pivot: Researchers observed two IP addresses that returned both Tier 1 certificates and different certificates:
- 84.110.122[.]27 – Returned both Tier 1 and “forti.external-Staging-02.com” certificates
- 178.237.39[.]204 – Returned both Tier 1 and “awake-wood.io” certificates
Now below is the global infrastructure of Paragon after analyzing all the 4 fingerprints
Paragon’s Technical Approach
Technical analysis revealed Paragon’s distinctive approach to spyware deployment:
- Process injection technique: Instead of deploying standalone malware, Paragon injects code into legitimate applications
- Target apps: WhatsApp and other popular messaging applications confirmed as infection vectors
- Detection evasion: Technique minimizes new processes, limiting typical forensic indicators
- Persistence mechanism: Maintains presence across app restarts and potentially system reboots
While Paragon’s approach makes traditional forensics more difficult, it potentially increases visibility to app developers who collect telemetry and crash reports.
Major Customers of Paragon
Australia
– Paragon’s infrastructure was traced to IP addresses in Australia, with domain names like external-astra.com and internal-Abba.com associated with Tier 2 servers.
– These deployments suggest Australian government or law enforcement agencies may be using Paragon’s spyware tools for surveillance purposes.
Canada
– A significant potential customer identified in Canada is the Ontario Provincial Police (OPP), based on IP address registrations.
– The research found evidence suggesting that the OPP might be using Paragon’s spyware tools, with one IP address associated with the OPP’s general headquarters.
Denmark: Domains like external-drt.com indicate potential use by Danish law enforcement or intelligence agencies.
Israel
– As the home country of Paragon Solutions, Israel is a primary customer of its own spyware tools. Domains like forti.external-muki.com indicate direct usage by Israeli agencies.
– Israel’s connection to Tier 2 infrastructure further highlights the use of Paragon’s spyware for domestic surveillance.
Cyprus: Paragon spyware infrastructure linked to Cyprus was observed, with IP addresses corresponding to domains like external-cag.com.
Singapore: IPs linked to domains like forti.external-sht-prd-4.com show Paragon’s presence in Singapore, possibly used by local authorities.
Germany: IPs from Digital Realty datacenters in Germany, hosting various codenames like “nelly” and “soundgarden,” point to European surveillance use.
Italy
– Italy is an admitted customer of Paragon’s spyware. Evidence of Paragon’s spyware targeting individuals in Italy was found, particularly among journalists and civil society members.
– The use of Paragon’s tools in Italy has raised concerns about the extent of surveillance and targeting of activists and journalists.
The Bottom Line
Paragon Solutions may market itself as a provider of ethical spyware solutions, but its infrastructure and global operations reveal a far more troubling reality. Operating in a gray area, the company exploits zero-day vulnerabilities in products to profit, creating numerous complexities. As the legal battle between Meta and NSO Group continues, Paragon’s activities are likely to spark a new wave of lawsuits across multiple countries.
Source: hxxps://citizenlab.ca/2025/03/a-first-look-at-paragons-proliferating-spyware-operations/
Related Reading: How Chinese Spyware Targeted US Nationals and CCP’s Critiques
Follow us on X and Linkedin for the latest cybersecurity news.