Dragon RaaS is a Russian Ransomware group that actively participates in hacktivism and cybercrime. It gained significant attention in July of last year when it became part of a larger cybercrime syndicate known as “The Five Families,” which includes ThreatSec, GhostSec, Blackforums, and SiegedSec.
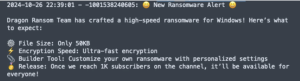
The group officially launched its operations in October 2024, announcing its first claimed victim—Al-Saeeda University in Yemen—on October 25. The following day, Dragon RaaS formally unveiled its “Dragon Ransomware RaaS Platform” through its Telegram channel, which currently has approximately 800 subscribers.
Infection Vectors and Exploitation Methods
The threat actor primarily gains initial access through:
- Exploitation of known web application vulnerabilities
- Brute-force attacks against administrative credentials
- Utilization of compromised credentials from infostealer logs
- Abuse of weak configurations (particularly default admin passwords)
The group has demonstrated particular interest in WordPress installations, targeting multiple vulnerabilities in the Porto WordPress theme:
- CVE-2024-3806: Poor input sanitization enabling Local File Inclusion
- CVE-2024-3807: Inadequate file input validation permitting LFI
- CVE-2024-3808: File handling weaknesses that facilitate LFI
- CVE-2024-3809: Validation errors resulting in LFI opportunities
Dragon RaaS systematically targets LiteSpeed HTTP servers with particular focus on directory traversal and remote code execution vulnerabilities. The group’s preferred exploit chain includes:
- CVE-2022-0073: Command injection vulnerability in LiteSpeed HTTP
- CVE-2022-0074: Privilege escalation in LiteSpeed HTTP
- CVE-2023-2359: Remote code execution in Slider Revolution (WordPress plugin)
- CVE-2023-6925: Command injection in WPBakery Page Builder
- CVE-2023-47784: Arbitrary file upload in Slider Revolution
- CVE-2024-47374: Cross-site scripting in LiteSpeed HTTP
A particularly efficient attack vector utilized by Dragon RaaS involves targeting exposed cPanel interfaces that manage multiple domains. By compromising a single cPanel instance, the group can simultaneously deploy their payloads to numerous websites, subsequently claiming each as a separate victim in their announcements.
Dual Ransomware Arsenal
Dragon RaaS employs two distinct ransomware variants:
1. PHP Webshell Encryptor
This PHP-based tool serves both as a backdoor and as a server-side encryption mechanism, primarily targeting web servers and file servers. Upon successful deployment, the webshell presents attackers with:
- File manipulation capabilities
- Directory encryption functionality
- Site defacement tools
- Decryption interface for victim communication
The PHP encryptor offers multiple encryption methods: OpenSSL (AES-256 in CBC mode), XOR, or mCrypt. When executed, the script:
- Recursively traverses directories from its installation point
- Encrypts files using the chosen method
- Deletes original files and replaces them with encrypted versions
- Appends the “.dragon” extension to all encrypted files
- Drops a Readme.HTML ransom note
- Retrieves additional ransom content from a Pastebin URL
2. Windows Encryptor
Contrary to Dragon RaaS claims of developing a unique ransomware variant, Windows encryptor is a rebranded version of StormCry ransomware with minimal modifications.
The Windows variant is distributed as a PyInstaller-packaged executable with the core ransomware functionality contained in worm1.pyc. Decompilation of this file reveals near-identical code between StormCry and Dragon Team ransomware, with the primary changes being:
- Modification of the file extension from “.stormous” to “.dragon”
- Updated branding in ransom notes from “StormCry” to “Dragon Team”
The rebranding attempt is incomplete, with multiple “Stormous” references remaining in the Dragon Team source code.
The encryption procedure follows a standard implementation:
- The malware enumerates local disks
- It targets 74 specific file extensions including documents, images, databases, and media files
- It skips system directories like Program Files, AppData, and System Volume Information
- Files are encrypted using AES-256 in CBC mode
- The AES key is then encrypted with the attacker’s RSA public key (embedded in the source)
- The RSA-encrypted AES key is written to the victim’s Desktop as “000keys.eky”
- All encrypted files receive the “.dragon” extension
- HTML and TXT ransom notes are written to the Desktop
Further technical evidence linking Dragon RaaS to StormCry includes the presence of a Bitcoin address (1DzX3w6Fb8yd78UMnWxfjnPQ14jWpEtVSA) in the Dragon Team source code that was previously associated with StormCry operations.
Both ransomware variants demand the same ransom amount ($300 USD in Bitcoin) and direct victims to overlapping Telegram channels (@StormousBot and @DragonRansom).
Victims
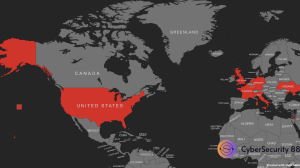
Dragon RaaS primarily targets organizations in:
- United States
- Israel
- United Kingdom
- France
- Germany
- Ukraine
- Netherlands
- Italy
The Bottom Line: All Bark No Bite
The group’s actual encryption activities appear less extensive than their defacement operations. Analysis of their Mirror-H profile (a platform documenting website defacements) shows numerous claimed victims that do not appear in their Telegram announcements, suggesting that many of their “attacks” may be limited to website defacements rather than true ransomware deployments.
Indicators of Compromise
SHA 256
111caef54a6bb02a11d8c6f923e5c8b1f2323eb3
1b4b4e910bfd31f5f3f2f3a269bf2c994978b78a
2a720281cd869c1aaaca430a96cf980f623e0f76
3afd36e7e837d7216bdb48e466f8dcd5f2b169b6
aa62afd6a48d3c42ed66d4f5b9189be847ec055b
Telegram IDs
@StormousBot
@DragonRansom
Network (Domains)
jso-tools.z-x.my[.]id JSO Injection
BTC Addresses
15dr6tJzJ2gXGJiYCtbr82yphEqhmaB8Mk
15W7LH9m4E1NaSCDCx2ovtfpugRwDztXj5
16fbxX2mrxUjbhkk2DamrzTiGN6JXhQsAu
17eiCc9BrhaqHLzvrqDNUVmVy4FUSoCT6f
1ADPdFTmjv4VSdHijjSAsDUKpBu4UuvaN1
1CA54B1kFjdXmFKNKv3W3KDRRGcW6r1pXP
1DxKVoke5Pb3UBfgUyJb4SHDNv95bCzAD8
1DzX3w6Fb8yd78UMnWxfjnPQ14jWpEtVSA
1G22LYkNAseuLRYxD2BVM8WYorc8w6cj8b
1G8jFCESzwWztfBJP7Ev23R4t9SFkPkZ5S
Follow us on X and Linkedin for the latest cybersecurity news
Source: hxxps[://]www[.]sentinelone[.]com/wp-content/uploads/2025/03/dragonteam_oct2024_preview.jpg