A set of five vulnerabilities, collectively called “IngressNightmare”, have been discovered in the Ingress NGINX Controller for Kubernetes, posing an immediate threat to over 6,500 Kubernetes clusters. These vulnerabilities could lead to RCE(Remote Code Authentication). The vulnerabilities, tracked as CVE-2025-24513, CVE-2025-24514, CVE-2025-1097, CVE-2025-1098, and CVE-2025-1974.
Vulnerabilities at a Glance
The Ingress NGINX Controller relies on NGINX as a reverse proxy and load balancer, making it a target for exploitation. These vulnerabilities are from the admission controller being accessible over the network without authentication.
1.CVE-2025-24513 (CVSS: 4.8)
This vulnerability involves improper input validation, which could cause directory traversal within the container. When combined with other 4 vulnerabilities, it could be used to carry out denial-of-service or expose secret objects.
2.CVE-2025-24514 (CVSS: 8.8)
The auth-url Ingress annotation allows attackers to inject malicious configurations into NGINX, which could result in arbitrary code execution.
3.CVE-2025-1097 (CVSS: 8.8)
The auth-tls-match-cn Ingress annotations also enable attackers to inject malicious arbitrary configuration into NGINX.
4.CVE-2025-1098 (CVSS: 8.8)
The mirror-target and mirror-host Ingress annotations can also be exploited to inject arbitrary configuration into NGINX. This could cause secret disclosure.
5.CVE-2025-1974 (CVSS: 9.8)
This vulnerability allows unauthenticated attackers with access to the pod network to achieve arbitrary code execution on the ingress-nginx controller.
How Attackers Could Exploit the Flaws
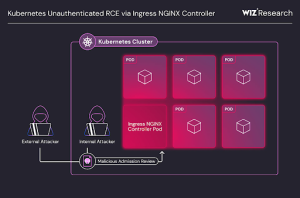
In a real attack scenario, an attacker could upload a malicious payload using NGINX’s client-body buffer features, followed by sending an AdmissionReview request using the aforementioned configuration injections. This results in the execution of malicious payload, allowing the attacker to gain remote control over Ingress NGINX Controller pod.
This chain could facilitate threat actors to take over a full cluster without credentials or administrative access.
Mitigation
The issues have been patched in Ingress NGINX Controller versions 1.12.1, 1.11.5, and 1.10.7. For immediate protection, users are urged to update to the latest version of the Ingress NGINX Controller and ensure that the admission webhook endpoint is not exposed externally.
Moreover,
Restrict access to the admission controller to Kubernetes API Server.
Temporarily disable the admission controller if it is not needed.
Source: hxxps[://]www[.]wiz[.]io/blog/ingress-nginx-kubernetes-vulnerabilities
Follow us on X and LinkedIn for the latest cybersecurity news.








