The Chinese cyber threat group FamousSparrow has been associated with a cyber attack that targeted a trade group in the United States and a research institute in Mexico, with the goal of deploying its primary backdoors, SparrowDoor and ShadowPad.
Background
FamousSparrow is a cyberespionage group with strong ties to China, active since 2019. This group is known for exploiting ProxyLogon vulnerability. Initially, FamousSparrow targeted international hotels, governments, law firms, and engineering companies.
Over time, FamousSparrow has refined its tools, with a particular focus on its proprietary backdoor, SparrowDoor, which remains exclusive to the group. While FamousSparrow were dormant for a period, they became active during 2024 deploying sophisticated versions of SparrowDoor and using modular and parallelized tactics that signaled significant progress in their operations.
Attack Chain
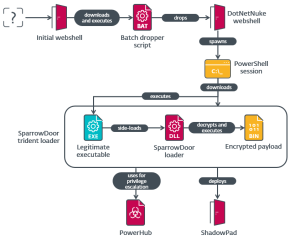
The threat actor utlized multiple custom tools, malware and tools used by Chinese APT groups, along with publicly accessible tools. The final payloads in this campaign were SparrowDoor and ShadowPad. A diagram (Figure 1) illustrates the entire attack chain
Initial Access
FamousSparrow gained initial access to the targeted network by deploying a web shell on an IIS server. While the exact exploit used for the web shell remains unidentified, victims’ systems were running outdated versions of Windows Server and Microsoft Exchange, for which there are multiple publicly available exploits.
- The attacker began by downloading a batch script via HTTP from the server at IP address 43.254.216[.]195.
- This script contains a base64-encoded .NET webshell, which it writes to the file path C:\users\public\s.txt.
- The script then decodes the webshell using certutil.exe and saves the decoded file to C:\users\public\s.ashx. The .ASHX file is an ASP.NET HTTP handler, similar to ASPX but it doesn’t have UI components.
WebShell Deployment
- The script starts by searching C:, I:, and P: to locate the installation directory of DotNetNuke.
- Then copies teh ASHX webshell to DotNetNuke_directory>\DesktopModules\DotNetNuke.ashx.
- The webshell encrypts all incoming and outgoing data using the hardcoded AES key e2c99096bcecd1b5.
Upon the first request, the webshell expects a .NET PE file, which it loads into memory and stores in a session variable. Upon next requests, it creates an instance of the LY class within the .NET assembly and passes the received data to the class’s Equals method.
While there has been no payload captured during this interaction, it appears that the Equals method is manipulating the data flow for remote PowerShell access.
PowerShell Session
After creating an interactive remote PowerShell session, attackers used legitimate Windows tools to gather more information about the host and the Active Directory domains.
- PowerHub, an open-source post-exploitation framework is downloaded using a server they control.
- To escalate privileges to SYSTEM level, the attackers deployed the BadPotato privilege-escalation technique.
While PowerHub does not contain any exploit by default, the attackers incorporated the open-source Invoke-BadPotato module into their setup.
Trident Loader Deployment
The attackers then used PowerShell’s Invoke-WebRequest command to download three files from the same server.The legitimate executable K7AVMScn.exe (K7AntiVirus Messenger Scanner) was used for DLL side-loading, while the malicious DLL and encrypted payload files were named K7AVWScn.dll and K7AVWScn.doc, respectively.
This process resembles the method described by the UK NCSC in 2022.
Payload Decryption and Execution
The payload is encrypted in K7AVWScn.doc and decrypted using an RC4 key that was hardcoded in the loader and payload. However, the RC4 key varied between different samples.
The decrypted payload contains custom configuration similar to the configuration outlined by the UK NCSC. The key difference was that the XOR key field in the first party of the payload was removed and the last 202 bytes of the payload were encrypted separately with the RC4 key. Moreover, it contains the command-and-control (C&C) server configuration.
Mitigation
-
-
- Adopt Multi-Factor Authentication (MFA) and Strong Access Controls.
- Implement Network Segmentation and Monitoring.
- Avoid using EOL products like Windows Server and Microsoft Exchange.
- Ensure that all systems are up to date with the latest security patches.
-
Source:hxxps[://]www[.]welivesecurity[.]com/en/eset-research/you-will-always-remember-this-as-the-day-you-finally-caught-famoussparrow/
Follow us on X and LinkedIn for the latest cybersecurity news.
Related Reading
Chinese Hackers: 4-Year Stay at Telecom Giant, No Check-Out!









