The Hellcat hacking group, which gained limelight in 2024, after a series of high-profile cyber attacks on major corporations like Schneider Electric, Telefónica, and Orange Romania. New research by KelaCyber has revealed the true identities of the group’s key members, Rey and Pyrx. Here’s a breakdown of their findings.
Key Details
-
- From an obscure group known as “ICA Group,” Hellcat quickly became notorious for its attacks.
- Rey and Pryx, two central figures in the group, are now identified through extensive OSINT research.
- Rey’s evolution: From an early hacker under the alias “Hikki-Chan” to a feared group leader in Hellcat.
-
- Pryx’s progression: A solo hacker who expanded into larger-scale attacks and malware distribution.
Structure of Hellcat Group
Hellcat’s organizational structure is deliberately designed for operational security and resilience. The group employs a zero-trust, cell-based architecture reminiscent of terrorist organizations, to limit the exposure of operational details in the event of a compromise.
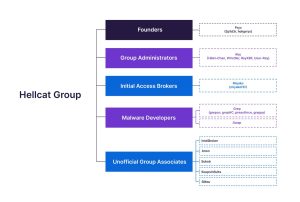
Leadership within Hellcat is decentralized, with multiple individuals holding administrative roles. Notable figures include “Rey,” who manages servers, oversees marketing, engages in negotiations, and participates directly in attacks; “Miyako,” who focuses on targeted breaches, particularly in sectors like finance, healthcare, and technology; and “Pryx,” who co-founded the group and contributes to malware development and initial access operations.
Connecting the Dots

OSINT research by KelaCyber identified Rey’s involvement with two infostealer infections in early 2024, tracing one of the compromised machines back to a young individual named “Saif” from Amman, Jordan. Rey’s prior user names, such as “ggyaf” and “o5tdev,” have been tied to hacking forums like RaidForums and BreachForums, along with platforms like GitHub and ProtonMail. A Pastebin post revealed Rey’s has ties with Anonymous Palestine.

Pryx’s connection to a specific malware strain was mapped via the website pato.pw, which he operated as a platform for both security researchers and his own malicious activities.
A key discovery was the use of the name “Adem” in an archived guide on pato.pw, which was later removed. This name led to a connection with an individual in the UAE, who was identified as having ties to the cybercriminal group WeedSec, suggesting a deeper network of collaboration among threat actors.
Opsec Mistakes That Led to Their Identification
- The big irony is that Rey and Pryx, who depended heavily on infostealer logs for their operations, ended up becoming victims of it themselves.
- Rey’s Forum Activity: Rey’s use of multiple aliases across hacking forums, along with identifiable information in his posts, made it easier to track him.
- Pryx’s Repository & Website: Pryx’s connection to the pato.pw website and a personal GitHub repository revealed key details about his identity.
- Key Slip-Ups: These operational security mistakes allowed investigators to connect the dots and uncover their real-world identities and cybercriminal networks.
Bottom Line
Rey and Pryx, the leaders of the Hellcat hacking group, made critical opsec mistakes that led to their identification. Digital traces, infostealer infections, and thorough analysis of their online activities allowed security researchers to link them to their real-world identities. Time is running out, and it’s only a matter of time before law enforcement agencies make their move.
Follow us on X and Linkedin for the latest cybersecurity news
Source:hxxps[://]www[.]kelacyber[.]com/blog/hellcat-hacking-group-unmasked-rey-and-pryx/







