North Korea’s infamous Lazarus Group, known for or cybercriminal activity aimed at funding the regime through cryptocurrency theft, is adopting a new “ClickFix” attack method. This latest campaign dubbed as “ClickFake Interview” is aimed to exploit job seekers. The move signals a shift in Lazarus group’s strategy, targeting less tech-savvy victims in the cryptocurrency sector.
ClickFake Interview Campaign
After Bybit’s $1.5B heist, Lazarus group is making waves with its ClickFake Interview Campaign, using clickfix attack method. According to researchers from Sekoia, this campaign follows a similar pattern to their earlier Contagious Interview operation, which targeted job seekers within the tech space. But this time, Lazarus is shifting focus, aiming to exploit employees within centralized finance (CeFi) organizations, such as Coinbase, KuCoin, Kraken, and Robinhood.
-
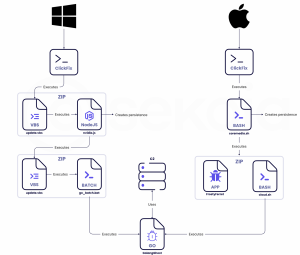
- The attack begins when Lazarus reaches out to job seekers via social media, luring them with a fake job interview opportunity on a cryptocurrency-related website.
- Victims are guided to a seemingly legitimate interview process that asks them to fill out forms, respond to crypto-related questions, and even create a self-introduction video.
- The plot thickens when users are asked to enable their camera. At this point, an error message appears, triggering the ClickFix method.
- The message instructs the victim to download a driver to fix the camera error.
This innocuous-sounding step is a carefully crafted ruse—victims are unknowingly prompted to copy, paste, and execute malicious code that compromises their system.
Depending on the operating system, the attack can lead to the deployment of either a bash script (targeting macOS) or a VBScript (targeting Windows). These scripts install a backdoor on the victim’s device, allowing Lazarus to exfiltrate sensitive data and take control of the compromised system.
Conclusion
The ClickFix technique is gaining traction among various cybercriminal groups, including Lazarus. First observed in 2024, this method involves a social engineering tactic where victims are tricked into downloading malware by convincing them to “fix” a non-existent issue on their device.
As this attack method continues to spread, it poses a serious threat to individuals and organizations in the cryptocurrency industry. The seemingly harmless actions, such as clicking on a link or downloading a driver, are powerful vectors for attackers to infiltrate systems and steal data.
Source: hxxps[://]blog[.]sekoia[.]io/clickfake-interview-campaign-by-lazarus/
Follow us on X and Linkedin for the latest cybersecurity news







