Cybersecurity researchers are raisng alarm over an increase in cyberattacks linked to notorious malware strain known as XorDDoS, which has been aggressively targeting systems in the United States. According to a new analysis by Cisco Talos, 71.3% of XorDDoS-related attacks between November 2023 and February 2025 were aimed at U.S. infrastructure.

XorDDoS
XorDDoS is a Linux-based distributed denial-of-service (DDoS) trojan that has been active for over a decade. DDoS stands for Distributed Denial-of-Service. It’s a type of cyberattack where a target (like a website, server, or network) is flooded with massive amounts of traffic from many different sources—all at once. The goal is to slow down or crash the system.
Attack Chain
The initial infection typically occurs via SSH brute-force attacks, where the malware forcibly gains access by trying numerous password combinations. Once access is gained, it installs itself, sets up persistence through startup scripts and scheduled tasks (cron jobs), and decrypts a built-in configuration to establish C2 communication.
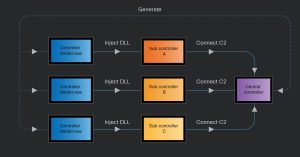
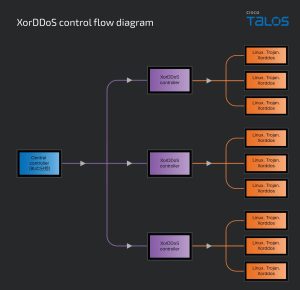
Cisco also discovered a new variant in 2024, dubbed as VIP version– which includes an updated sub-controller, a central command controller, and a malware builder tool. This suggests that XorDDoS may now be sold as a malware-as-a-service offering on underground markets.
The central controller manages multiple sub-controllers, each commanding a botnet of compromised devices to launch synchronized DDoS attacks. Language settings within the malware indicate the operators are likely Chinese-speaking individuals.
Impact
The Talos report highlights a significant spike in XorDDoS activity between 2020 and 2023, noting that the malware’s reach has extended beyond traditionally exposed Linux systems to include Docker servers. Geographically, nearly 42% of infected devices are based in the United States, with other affected countries including Japan, Canada, Denmark, Italy, Morocco, and China.
Conclusion
Experts recommend organizations strengthen SSH credentials, monitor for unusual network traffic, and apply security patches regularly to reduce the risk of infection. Moreover Set up rate limits and intrusion detection systems.
Source:hxxps[://]blog[.]talosintelligence[.]com/unmasking-the-new-xorddos-controller-and-infrastructure/
Follow us on X and Linkedin for the latest cybersecurity news