A ransomware group has targeted a utility billing software provider by taking advantage of a serious vulnerability in a remote monitoring tool called SimpleHelp. This tool is widely used by managed service providers (MSPs) and IT support teams to access systems remotely. Unfortunately, attackers have found a way to abuse it to launch ransomware attacks.
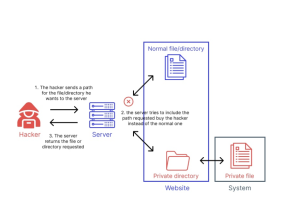
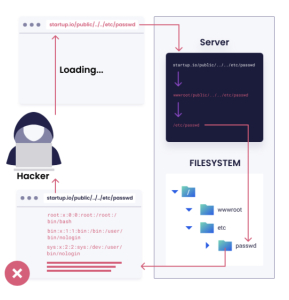
The flaw used in this attack exists in older versions of SimpleHelp, particularly versions before 5.5.8. Security researchers identified this as CVE-2024-57727, which allows attackers to perform a “path traversal” — a technique that helps them access files they shouldn’t be able to reach. Once inside, they can upload harmful files and take control of the system.
The breach happened when attackers used this weakness to gain access to the remote support environment of a utility billing firm. They then pushed ransomware to downstream clients and systems, launching what’s known as a double-extortion attack. This means they not only locked files but also stole data to pressure the company into paying a ransom.
Experts believe the ransomware group known as DragonForce may be behind this attack. The same group has previously been seen using SimpleHelp vulnerabilities to compromise networks and spread ransomware. Their method usually involves deploying malicious files, stealing data, and encrypting systems — all while remaining unnoticed for as long as possible.
The U.S. government’s Cybersecurity and Infrastructure Security Agency (CISA) issued an alert urging all SimpleHelp users to update their systems immediately. They highlighted the importance of patching older versions and warned that outdated SimpleHelp installations are becoming a top target for attackers.
CISA’s advice is very clear. If you’re using SimpleHelp, you should:
- Immediately upgrade to the latest version.
- Disconnect any vulnerable servers from the public internet.
Monitor for suspicious behavior, like unknown files appearing on devices. - Review access logs and check for unauthorized activity.
The agency also warned about indicators of compromise, such as files named aaa.exe and unusual outbound traffic to suspicious domains. These are signs that attackers may already be active inside your network.
This incident shows how attackers are shifting their focus to third-party tools that are trusted by businesses. Remote monitoring and management (RMM) tools like SimpleHelp are often left exposed to the internet and aren’t always updated as quickly as they should be. That makes them a high-value target for ransomware gangs.
What’s especially dangerous is that these kinds of attacks often hit multiple organizations at once. Since MSPs serve several clients, compromising one RMM system can lead to widespread damage. That’s why attackers love using this approach.
In today’s cybersecurity landscape, keeping software updated is no longer optional. It’s essential. This case is a reminder that even small tools like remote support software can open the door to big threats if left unpatched.
Stay alert, and keep your security measures updated!
Source: Follow cybersecurity88 on X and LinkedIn for the latest cybersecurity news