A sophisticated new malware strain called “Arcane” is targeting gamers through YouTube videos and steal wide range of sensitive data from VPN, gaming clients, and network utilities like ngrok, Playit, Cyberduck, FileZilla and DynDNS.
How Arcane Stealer Works
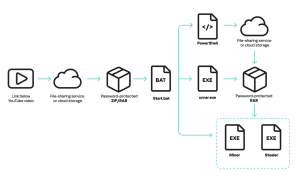
Arcane Stealer Distribution(Source:Securelist)
The initial attack begins with YouTube videos promoting game cheats, leading users to download password-protected archives containing malicious batch files. This archives contain
Obfuscated batch files that appear legitimate
The UnRAR.exe utility hidden in subfolders
Instructions that convince users to execute the files
When executed, the malicious batch file:
- Downloads a second password-protected archive via PowerShell
- Uses the embedded password to unpack the archive automatically
- Adds system drive roots to SmartScreen filter exceptions
- Disables Windows SmartScreen protections by modifying registry keys
- Launches the extracted malware executables
- Downloads additional malicious payloads
- Installs both cryptocurrency miners and the data-stealing trojan
Impact
- The malware targets over 10 VPN clients including NordVPN and ExpressVPN
- It steals data from at least 6 gaming platforms including Steam and Epic
- Most victims are located in Russia, Belarus, and Kazakhstan
What they’re stealing
Arcane collects an extensive range of data:
- System information: OS details, hardware specifications, screenshots, and location data
- Credentials: Passwords from browsers, email clients, and messaging apps
- Financial data: Credit card information and cryptocurrency wallet contents such as Zcash, Armory, Bytecoin, Jaxx, Exodus,etc.
- Gaming accounts: Access to Steam, Epic, Roblox, and more
- Network configurations: Including saved Wi-Fi passwords and VPN settings
The Staler also launches a copy of the browser using “remote-debugging-port” argument, then connects to the debug port, issues commands to visit sites with more personal data, and requests their cookies
The list of sites it visits are provided below.
- https://gmail.com,
- https://drive.google.com,
- https://photos.google.com,
- https://mail.ru,
- https://rambler.ru,
- https://steamcommunity.com,
- https://youtube.com,
- https://avito.ru,
- https://ozon.ru,
- https://twitter.com,
- https://roblox.com,
- https://passport.yandex.ru
The bottom line
Security experts warn users to be skeptical of free cheats and cracks, avoid links from unfamiliar content creators, and maintain updated security software as this threat continues to evolve.
Related Reading: DCRat Backdoor’s Comeback
Source: hxxps[://]securelist[.]com/arcane-stealer/115919/
Follow us on X and Linkedin for the latest cybersecurity news.