Ukraine’s Computer Emergency Response Team (CERT-UA) has discovered another sophisticated cyber espionage campaign that has been targeting Ukraine’s key national security institutions like military innovation centers, armed forces, Law enforcement agencies, and local governments—particularly in regions along the country’s eastern border.
According to CERT-UA, the cyber threat activity, tracked under the identifier UAC-0226, has been ongoing since February 2025 and it’s primary motive is espionage.
Attack Chain
The initial access relies heavily on email phishing campaigns, with malicious attachments to exploit common administrative and military themes. The attack begins with the distribution of emails with Excel spreadsheets with embedded macros (.xlsm files). These documents are designed to look legitimate, often using subjects related to demining operations, administrative penalties, UAV production, and compensation for war-related property damage.
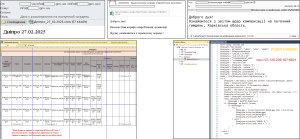
CERT-UA reports that threat actors have used compromised email accounts, including access via webmail interfaces, to distribute these phishing messages.
Once opened, the macros execute embedded Base64-encoded payloads hidden within spreadsheets. These payloads are decoded into executable files that are saved to victims’ systems without extensions, making them harder to detect by before they are launched.
As of April 2025, CERT-UA has identified two primary malware strains used in these attacks:
1.A .NET-based tool embedding a PowerShell reverse shell script, sourced from a public GitHub repository (PSSW100AVB). This powershell faciliates remote control of infected systems.
2.GIFTEDCROOK, a powerful C/C++ data-stealing utility, which targets Chrome, Edge, and Firefox browsers. It extracts cookies, browsing history, and stored login credentials, then compresses the stolen data using the Compress-Archive PowerShell cmdlet and exfiltrates it via the Telegram.
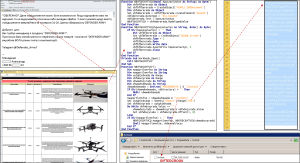
These malware are typically installed in seemingly legitimate directories such as:
- %PROGRAMDATA%\Microsoft OneDrive Assistant\
- %PROGRAMDATA%\Windows Telemetry\
- %PROGRAMDATA%\SysAnalyzer\
Indicators of Compromise (IOCs)
CERT-UA has shared detailed file hashes and host paths associated with the attack, including files named:
- Compensation for destroyed property.xlsm
- Administrative penalties of employees of the organization 921867.xlsm
- Defender ARMY Promotion (2).xlsm
- (GIFTEDCROOK) ServiceHub, SysAnalyzer, Svchost
- 149[.]102.246.110
- 37[.]120.239.187:6501
- 89[.]44.9.186:3240
Conclusion
While CERT-UA has not officially named a specific threat actor, the tactics, techniques, and procedures (TTPs) observed in this campaign bear notable similarities to those used by state-sponsored cyber espionage groups with a history of targeting Ukraine and its allies.
Given the ongoing conflict between the nations, the attack may have been carried out by Russia or its allies—such as Belarus, Iran, or North Korea—either through state-sponsored operations or affiliated hacking groups.
Follow us on X and Linkedin for the latest cybersecurity news
Source:hxxps[://]cert[.]gov[.]ua/article/6282946