A newly identified phishing-as-a-service (PhaaS) platform called Lucid has been found targeting more than 169 organization across 88 countries. The platform uses smishing technique via Apple iMessage and Rich Communication Services (RCS) on Android to orchestrate large-scale phishing attacks.
Why It Matters
Lucid’s methodology represents a drastic shift from traditional phishing techniques. By utilizing widely used communication methods like iMessage and RCS, cybercriminals can bypass standard spam filters, significantly increasing their chances of success. This advancement reflects the growing sophistication of cyber threats and the challenges faced by existing security infrastructures.
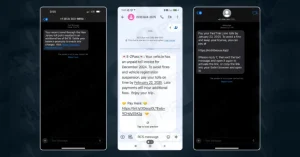
As per experts, the Lucid’s backend’s is coded using the Webman PHP framework, allows tracking phishing activity in real-time. The panel’s features include automated phishing website creation with customizable templates, IP blocking, user-agent filtering, and the use of time-limited, single-use URLs. These capabilities make Lucid a formidable tool in the phishing-as-a-service landscape.
The Bigger Picture
- Subscription Model: Lucid operates on a subscription basis, allowing cybercriminals to conduct large-scale phishing campaigns. The platform’s primary objective is to harvest credit card data and other personally identifiable information (PII) to commit financial fraud.
- Lucid takes advantage of Apple iMessage and Android RCS to evade spam filtering.
- The phishing campaigns often target regions like Europe, the UK, and the US. The attackers utilize iPhone device farms and mobile device emulators on Windows systems to send vast numbers of scam messages.
- To work around iMessage’s link-clicking restrictions, attackers use two-way communication prompts like “please reply with Y.” On Android, they frequently change sending domains and numbers to avoid RCS filtering.
Attribution
Researchers attribute Lucid to the XinXin group (also known as Black Technology), a Chinese-speaking hacking organization. The group is known for developing other PhaaS platforms like Lighthouse and Darcula, both of which have sophisticated features, including the ability to clone any website to create deceptive phishing pages. The group markets these tools on Telegram, offering subscription-based access to cybercriminals seeking to execute phishing schemes.
The rise of Lucid coincides with a broader surge in PhaaS incidents. Reports indicate that recent attacks have also leveraged other platforms like Tycoon 2FA, EvilProxy, and Sneaky 2FA.
Follow us on X and Linkedin for the latest cybersecurity news









