A targeted cyberattack on Uyghur exiles and senior members of the World Uyghur Congress (WUC) has been reported by Citizen Lab. It is believed to be orchestrated by threat actors linked to the Chinese government.
In March 2025, WUC members living in exile were subjected to a spear phishing campaign that delivered Windows-based malware disguised as a legitimate Uyghur-language word processor. The compromised software, a trojanized version of the open-source application UyghurEditPP, was originally developed by a trusted member of the Uyghur software development community.
While the malware was not highly sophisticated in its technical features, researchers say its delivery method was very precise and culturally attuned to its targets. This malicious campaign shows preparation dating back to at least May 2024.
Attack Chain
The malware was delivered via an email sent to WUC members from an individual impersonating as partner organization. The email linked to a password-protected RAR file hosted on Google Drive, containing the trojanized UyghurEditPP installer. Google’s threat analysis team had earlier sent government-backed attack alerts to the affected individuals on March 5, prompting them to involve researchers at the University of Toronto’s Citizen Lab.

The malicious version of UyghurEditPP contained a hidden backdoor called GheyretDetector.exe, capable of profiling the victim’s computer, uploading or downloading files, and executing commands via custom plugins. This functionality would allow an attacker to conduct persistent surveillance on Uyghur activists and their networks.
Infrastructure with Cultural Significance
The malware’s command and control (C2) infrastructure used domains with deep cultural relevance, including tengri.ooguy.com (Tengri meaning “Sky” or “Sky God” in Turkic languages) and anar.gleeze.com (Anar meaning “to remember”). Both domains were hardcoded into the backdoor and resolved to IP addresses associated with AS20473, a network often abused by threat actors and managed by Choopa LLC.
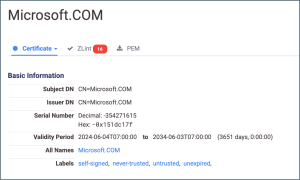
A fake TLS certificate impersonating “Microsoft.COM” was found on the C2 servers. With a non-compliant serial number and outdated encryption standards, the certificate was clearly not intended for legitimate use, according to Censys data.

Researchers also discovered earlier infrastructure registered under the names gheyret.com, gheyret.net, and uheyret.com, designed to impersonate the real UyghurEditPP developer. Though not used in the WUC attack, the existence of this infrastructure shows the attackers had planned for multiple vectors of infiltration.
Link to Chinese Threat Actors
While Citizen Lab stopped short of attributing the operation with full certainty, the campaign’s techniques and target choice align closely with known Chinese state-sponsored operations. These include the targeting of Uyghur, Tibetan, and Taiwanese communities using spyware disguised as language apps or religious tools.
The UK’s National Cyber Security Centre recently issued a related warning, citing similar abuse of benign cultural apps to target exiles and diaspora groups.
Tabled evidence from this case echoes findings from prior Citizen Lab investigations and data leaks, including the 2024 I-Soon leak that exposed commercial spyware operations tied to Chinese state interests.
Final Thoughts
The campaign against the WUC is a potent reminder that the digital sphere is now an active front in the fight for human rights. This campaign against Ugyhur shows how a community’s cultural identity can be weaponized against it through targeted phishing attacks.
The discovery of additional malware samples on VirusTotal—with variations in compile times and command-and-control domains—suggests a broader operation, possibly unfolding in phases or conducted in parallel to target other Uyghur individuals and organizations.
Source: hxxps[://]citizenlab[.]ca/2025/04/uyghur-language-software-hijacked-to-deliver-malware/
Follow Cybersecurity88 on X and Linkedin for the latest cybersecurity news









